Now that most of us are working from home, and “Zoom-Bombing” is a new worry, let’s review some good UC security practices.
There are three components to ensuring enterprises and users are being safe:
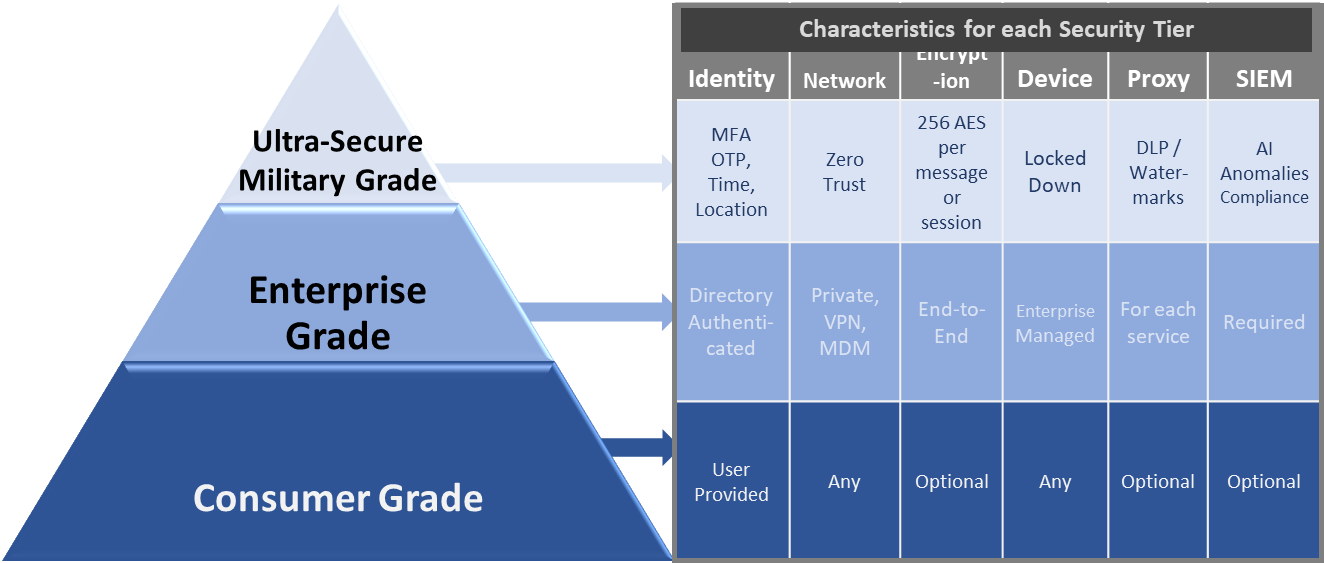
- Follow the Enterprise UC Security Framework — Multi-Factor Authentication (MFA), Zero Trust Networking (ZTN), end-to-end encryption, a securely managed device, Data Loss Prevention (DLP) via proxies, and integration with the enterprise Security Information and Event Management (SIEM) are essential. However, not all UC interactions require the same amount of security.
- Ensure UC Security is Convenient — External customers and internal users will bypass security controls if they add too much friction to the interaction. Customers will take their business elsewhere, and users will choose their own devices and freemium UC services. Users demand instantaneous access while getting the best protection possible as seen with the rapid adoption of password-less access to our cell phones via face and/or finger biometrics.
- Don’t Forget Privacy — Private information, which is data that can be used to identify you, and confidential data, which is data that you do not want to make public such as health and wealth, needs to be treated with the utmost security. It is ok to store someone’s preferences, history, and other information that is not private. Too often, enterprises store all customer information the same way and copy it a hundred times throughout the enterprise. Then they are surprised when it gets stolen.
The Market Responds to UC Security
Zoom focused on convenience, and now, they are being judged by not having enterprise-grade security and ensuring the privacy of their users. It’s a hard trifecta to manage.
Journey is a new start-up, led by Brett Shockley, that has come up with a solution to solve the security trifecta, and this is one of the reasons that they were voted this year’s Best of Enterprise Connect. Journey offers a Trusted Identity Platform, which solves security, privacy, and customer experience with no tradeoffs. The Internet was created without an identity layer, which has led to a bunch of point solutions, but those still don’t provide adequate security.
One Journey use case is that it can help ensure that an outbound call reaches a customer. With Journey, a bank, for instance, can give a user a "heads-up" notification that a call is coming. When the user answers the call, they can verify their identity via a faceprint and/or other information and be connected. Part of Journey's secret sauce is that it does this with a Zero Knowledge Proof, which shares a user’s secret attributes without actually sharing them, keeping their information private, and preventing the bank from needing to store the data.
For more on this topic, see the many No Jitter articles and webinars. Also, join us in early Aug. at Enterprise Connect, where we will have both a session on UC security along with a panel discussion on it. Until then, be safe!