Businesses have experienced persistent attacks on their IT infrastructure in 2023 and it looks like that trend will continue in 2024. According to Cisco, crypto mining, phishing, ransomware, trojans, and command and control were the leading attack types in 2023. The challenge for business and technology leaders is how they are going to defend against these attacks. We do not have hobbits, wizards, dwarves, elves, and kings to save our systems from the evils of the Internet. (Yes, I recently rewatched The Lord of the Rings)
However, we do have five heroes on our side. These technological heroes are:
- An Educated Human Firewall – Security policies, awareness training, and testing
- Unified Device Management – Policy-driven onboarding, offboarding and everything in-between
- Advanced Identity and Authentication Management – AI-powered zero trust enforcement
- A Perimeter-less Network – always behind the security edge
- Advanced Endpoint Protection – AI-powered extended detection and response
These heroes are not new, but they have matured so that every business can take advantage of their protection. The maturing of these solutions has seen them move to the cloud, available to businesses on a per-user subscription basis, as well as incorporating AI-powered data analytics capabilities that enable faster and more accurate protection, detection, and response.
These tools do not replace good cybersecurity management and operations practices, but they can give you a fighting chance against the enemy. Understanding the applications and tools used by the business will be more important than ever in managing cyber risks. However, these next generation tools do provide cybersecurity and IT teams with the detection and response capabilities using human and artificial intelligence (AI) to defend the business realm.
Educated Human Firewall
It is not a new concept that phishing and social engineering are still the most pervasive entry methods for compromising a network. Humans have always been the weak link in the security chain. The most effective way of reducing this risk is to make sure that your employees are aware of the corporate security policies and the reasons for their existence; paired with the regular training and testing of their ability to detect hackers’ attempts to compromise their accounts. There are many cost-effective SaaS solutions for testing and training staff that include current cybersecurity training content. Regular training should align with the corporate cybersecurity policy, and testing results should be used to reinforce the importance of training.
The limited availability of skilled and experienced cybersecurity resources to manage cybersecurity and respond to incidents will become more challenging for businesses in the coming years. Businesses will need to rely on better, AI-capable tools so existing resources can be more effective.
Unified Device Management
As business has moved to cloud for both applications and infrastructure, the most prevalent attack surface has become the devices or endpoints. These range from typical workstations, laptops, and smartphones to the less obvious sensors, smart screens, and other IoT devices. All of these devices need to be monitored and maintained in a secure, compliant, and up to date state.
Device management should be incorporated into staff onboarding and offboarding to ensure that any device that has access to corporate data is managed.
Most current device management cloud platforms are available on a per user or device subscription basis and can on-board a device automatically and streamline management by policy. They use declarative state policies to maintain ongoing compliance using AI to optimize the security of the device. They will manage and monitor a full range of devices to enable your cybersecurity resources to keep on top of things.
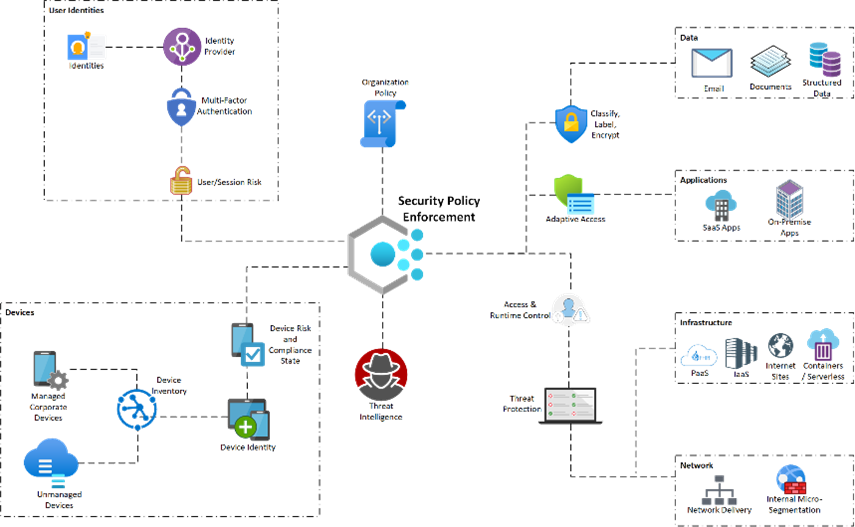
Advanced Identity and Authentication Management
Many are already familiar with managing user identities, access, and authentication, but it has become one of the most challenging cybersecurity risks. Username and passwords, no matter how obscure or complex, are no longer sufficient. MFA (multi-factor authentication – something you know and something you have) is now a minimum requirement for authentication.
The authentication platform needs to be easily integrated with applications to reduce the number of passwords that users need to use – SSO (single sign-on). This ensures that users have a strong access and authentication mechanism to protect all corporate data.
Advanced identity and authentications need to go further and use AI to consider a wide range of authentication factors including device compliance, user session risk, and network access location to enforce a zero-trust policy architecture. These cloud platforms are available on a per user subscription basis with more advanced features that can be licensed and configured for advanced cybersecurity capabilities. The recent introduction to password-less authentication is in its infancy but shows potential.
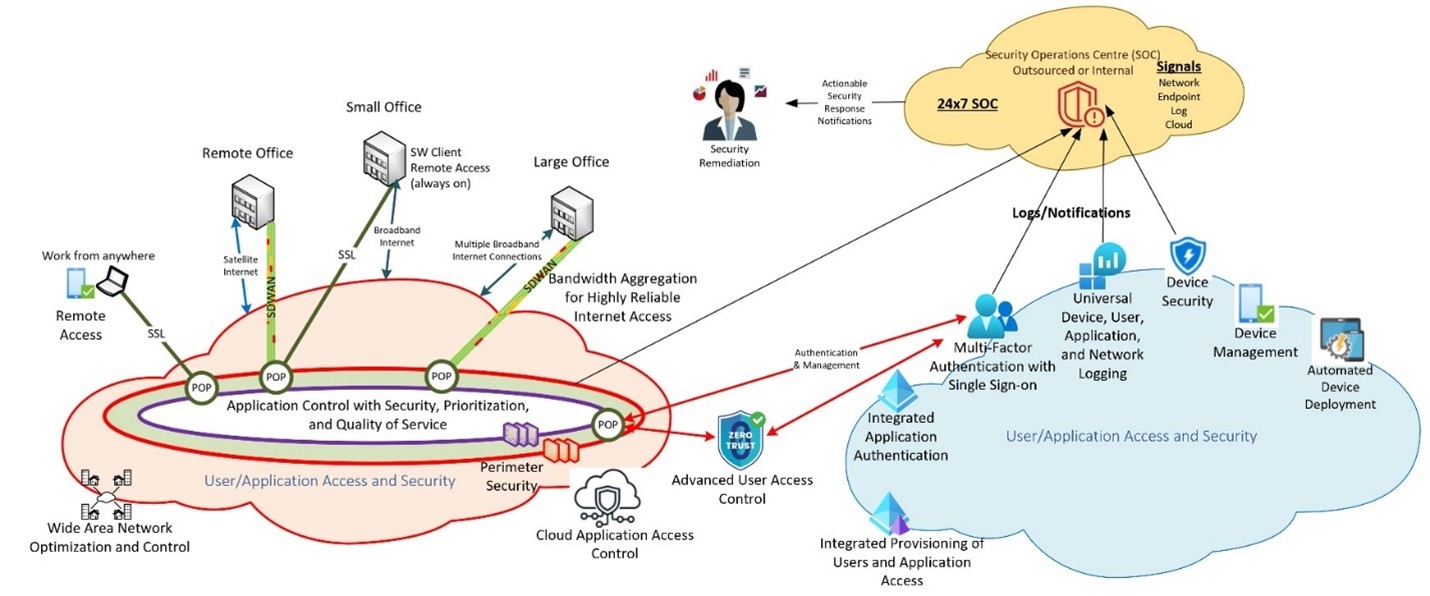
Perimeter-less Network
The new reality of the work from the remote-working, geographically independent employee has been a challenge for businesses and cybersecurity teams. The security of the communications of these remote users needs to be addressed by ensuring the user, device, communications, applications, and data are always behind the security edge. The user, data, and applications can be anywhere (cloud, on-premises, or hybrid). The borderless nature of business means that perimeter security, traditionally a firewall, needs to become perimeter-less.
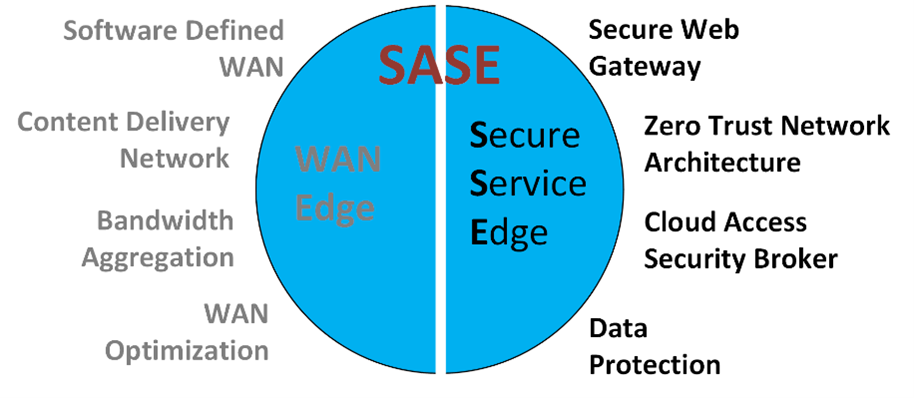
The perimeter-less nature of security can be accomplished using SASE (Secure Access Service Edge) or SSE (Secure Service Edge) technologies. Both architectures/services provide advanced next generation security that enables real time security detection and protection. These security architectures are available on a subscription basis with more advanced features that can be licensed and configured for advanced cybersecurity capabilities.
Advanced Endpoint Protection
Perhaps the greatest advancement in cybersecurity over the last decade has been Extended Detection and Response (XDR) endpoint security. Unified cybersecurity solutions use a combination of endpoint applications and cloud-based tools to collect and analyze data from multiple sources to detect, stop, and remediate cyberattacks using AI-powered analytics. They provide cybersecurity professionals with the tools to trace potential intrusions (often spiderwebs of attempted compromises) and eliminate vulnerabilities.
These solutions save your cybersecurity team time by automating the mundane aspects of threat hunting and enable them to be more proactive and respond in near real-time to potential threats.
The reality of today’s borderless businesses is that they are constantly under attack. All sectors are being targeted but financial services, healthcare, manufacturing, and government organizations seem to be hacker favorites due to the value of data, financial impact, and public impact of disruption of services. In 2024, make sure your cybersecurity team has these five technological heroes on your side.
Scott is writing on behalf of the SCTC, a premier professional organization for independent consultants. Our consultant members are leaders in the industry, able to provide best of breed professional services in a wide array of technologies. Every consultant member commits annually to a strict Code of Ethics, ensuring they work for the client benefit only and do not receive financial compensation from vendors and service providers.