Cyberattacks continue to make headlines as hackers target an ever-growing number of organizations lacking comprehensive security measures. Particularly vulnerable to system intrusions are VoIP (Voice over IP) communications, responsible for converging data and voice traffic onto a common IP network. With the proliferation of remote work, VoIP technology has replaced traditional phone lines to cut costs and handle the sudden influx of data the pandemic spawned. Additionally, with the rise of remote work, unified communication (UC) services like Zoom and Microsoft Teams (among others) have emerged as a prime target for hackers. Traditional firewalls are not enough to prevent the loss of critical confidential business information. And there’s no sign of stopping; the global VoIP market is expected to reach $327.5 billion by 2031.
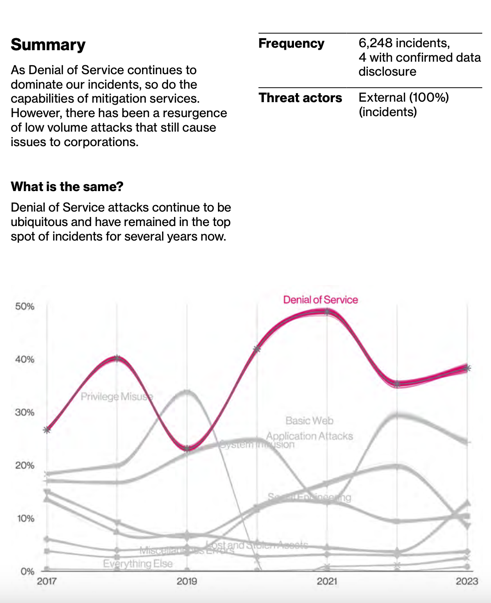
As attacks continue, Verizon’s latest Data Breach Incident Report divulges that denial-of-service (DoS) attacks top the list of attack patterns.
Appearing in 42% of all incidents, the frequency of these attacks, which aim to shut down a machine or network by flooding the target with traffic, are higher than both ransomware and phishing. DoS and distributed denial-of-service (DDoS) attacks, which use multiple computers or machines to flood a targeted resource, represent a major threat to all organizations; they put critical systems at risk, have significant financial consequences, undermine service level agreements, and cause reputational harm. Under pressure to maintain business continuity, enterprises should take stock of the current DoS landscape and implement a variety of measures designed to protect voice communications from DoS and DDoS attacks.
Common Attacks on VoIP Services
Since the introduction of VoIP technology, attackers have seized the opportunity to upskill their hacking methods to better infiltrate systems. Some of the most common strategies hackers employ today to disrupt VoIP network services – many of which can be combined to increase the probability of overloading a target’s network – include the following:
- Volumetric attacks: Through volumetric attacks, hackers aim to overwhelm networks with massive amounts of traffic, forcing servers to collapse under the bandwidth demands. Attackers spoof victims’ source addresses to send requests to server hosts, also known as a reflector server. As a result, the ensuing reply from the server generates an unusually large volume of traffic that compromises network operations.
- DDoS-For-Hire-Services: For-hire services enable attackers to carry out multiple attacks at once, making it difficult for organizations to identify which specific attack is delivering the most damage and confusing efforts to combat them. These attacks often remain undetected in early stages due to their low cost of entry, which enables a single individual or small organization to instigate such an attack.
- Small Packet Size: Small network packet sizes, typically under 100 bytes, help attackers fly under the radar to evade detection and covertly cause harm. In early stages, they can also act as a convenient stepping stone to larger, more severe attacks later on.
- Multi-Vector: A multi-layered DDoS approach attacks multiple SIP signaling ports that host services in order to overwhelm networks. This method ensures attackers can take down networks by the usage of multiple entry points.
- Use of Botnets: Sometimes a direct line is the quickest way to a successful attack. Hackers are turning towards botnets, short for “robot network,” to launch direct path attacks which target individual organizations. These often will be application-layer attacks, which target an application (e.g., web servers, SIP voice services) and specific vulnerabilities or issues. Volumetric attacks are also accomplished through the use of botnets.
Reevaluate Existing Defenses
Networks will continue to be compromised by attacks unless enterprises invest in robust defenses. To reduce the likelihood of a successful attack, enterprises should reevaluate their existing defense strategy, starting with implementing behavioral analytics and machine learning technology that can automate the detection and mitigation processes. According to a Metrigy survey, while over 90% of IT leaders believe voice security is important, only 49% have implemented a security solution. To ensure they’re integrating a solution with the most comprehensive security available, enterprises should evaluate for the following features:
- Reputation Scoring: Machine learning tools provide a reputation score for enterprises to drive decision-making during call setup about policy and procedures. These reputation scores are based off of real-time data that determines the relative “safety” of a call.
- Policy Enforcement: The most critical component of protecting a VoIP infrastructure is prevention. A session border controller, or SBC, can help drive effective policy making decisions by controlling the way calls cross over into an enterprise’s contact center or corporate network.
- Threat Visibility: Comprehensive dashboards and reporting provide a 360 degree look at VoIP threats for investigations and troubleshooting, ensuring a voice analytics solution is working as intended and can successfully stop bad actors.
For enterprises who choose to deploy “as a service” VoIP solutions, these security requirements still apply. While SaaS vendors will assume most of the security responsibilities that are typically taken on by customers who use on-premises technology, the security of their service offers will only be strong as their latest update. Without regular updates and maintenance, security flaws and vulnerabilities could go unnoticed. To ensure the highest level of protection, enterprises should expect their “as a service” VoIP provider to supply reports showing the quality of the security for their traffic.
In addition, it should come as no surprise that an enterprise should strongly consider maintaining their own SBC for added security protection as a complement to what their “as a service” VoIP provider delivers.
Although VoIP has risen in popularity due to its ability to reduce operating and equipment costs, the technology can be a significant source of security risks. Don’t let hackers be the first to identify gaps in your security infrastructure before you do. By adopting a few security initiatives, enterprises can rest easy knowing their name won’t make the next security breach headline.