You may have business relationships with an internationally located vendor, supplier, provider, contractor, employee, or customer. You may have boosted cybersecurity in your network. Be vigilant, attackers can use your business relationships as stepping-stones into your network.
The “
2019 Trustwave Global Security Report,” an extensive 76-page document, provides insight into some positive cybersecurity trends, showing that organizations are doing the right things to improve their cybersecurity stance. But it’s not all good news, as an endless stream of vulnerabilities and exploits persists.
A Host of Observations
Trustwave compiled its report based on observations and investigations conducted by its SpiderLabs team of malicious data breaches affecting thousands of systems located in 19 countries. Attackers seem to be shifting their focus away from the Americas to Asia-Pacific, mainly targeting businesses in Australia, Singapore, and Hong Kong. Although Trustwave covered many different types of incidents, I’ve focused on the network issues.
Some of the report’s conclusions are:
- The median number of days between intrusion and detection for external incidents dropped from 83 to 55, an improvement
- The median number of days from intrusion to detection for internal incidents was 11 days
- The industries most affected were retail, at 18% and financial, at 11%
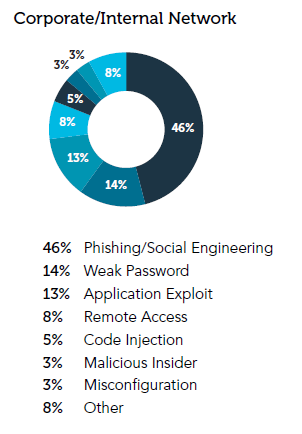
- Phishing accounted for 46% of the internal corporate network compromises
- Email attacks increased from 36% in 2017 to 45% in 2018
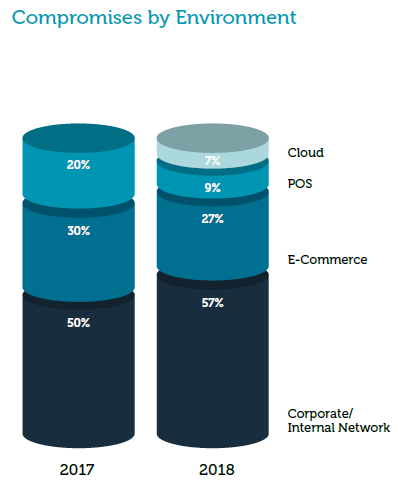
As shown in the graphic below, corporate and internal network compromises have increased from 50% in 2017 to 57% in 2018.
Network Security
In its internal and external network vulnerability scans, Trustwave inspected servers for insecure configurations that could increase attack risk and provide insights for attackers into the most frequent network vulnerabilities.
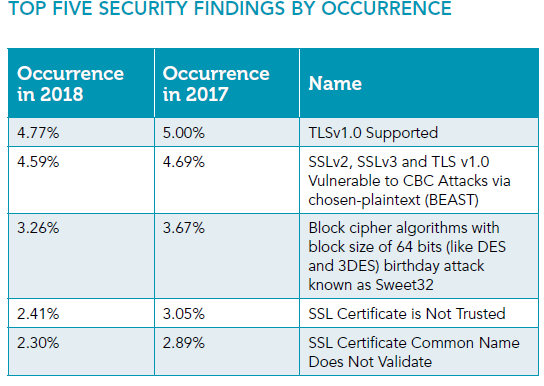
The vulnerabilities involving SSL and TLS protocols continue to be in the top five on Trustwave’s list. The top two findings involved servers that supported SSL 3.0 and earlier versions, and TLS 1.0. In its report, Trustwave advises website owners to stop supporting these insecure protocols and standardize on the newer versions. Trustwave increased notifications of the severity of the SSL and TLS findings, using language such as “SSL certificate is not trusted” and “SSL certificate name does not validate properly.”
The risk of using these protocols and trusted certificates should encourage the use of more secure encryption protocols. However, only a small handful of Web clients support the more secure protocols. As can be observed in the chart below, the number of security occurrences have dropped minimally from 2017 to 2018.
The other vulnerability mentioned in the top five security findings by occurrence relates to block cipher algorithms that use 64-bit blocks. These algorithms are vulnerable to an attack called Sweet32. The obsolete block cipher algorithms are fortunately only used in a small minority of HTTPS connections. Server administrators should discontinue the obsolete block cipher algorithms and support encryption schemes such as the Advanced Encryption Standard (AES).
The Problems Are Here
The end user remains the weak point in most breaches. Phishing (4%) and other social engineering techniques were the most common methods of compromise. Weak passwords and application exploits combined with phishing account for 73% of the problems. This is true no matter in which environment the end user was operating, as shown below.
Businesses should implement endpoint protection and response as well as antivirus software that can detect malicious activities and malware. Unfortunately, if a user gives away credentials, then the attacker’s activities can look like legitimate actions. The report recommends multifactor authentication (MFA) as the simplest and most-effective method for defending against these types of breaches. If you’re considering cloud services and they don’t have MFA, you shouldn’t do business with that provider.
Businesses can expect a wide range of attack methods to be used against their applications, systems, and networks. In the report, Trustwave observed that Internet-exposed intranets and development systems aren’t firewalled as much as they should be. The final recommendation is to use a simple vulnerability scan to detect improperly exposed systems.