As the world shifts back to the new normal, business faces a new challenge. Many workers found remote or hybrid work was a better way to work. If businesses accept the new normal of hybrid work, changes will be required to optimize how technology is used by the business and how they keep things secure.
This was historically challenging from a technology and a people perspective. In the past few years, technology has matured to simplify and enhance the security and user experience.
The Problem
These statements are still true today, but the risks are higher. Ransomware has matured to Ransomware as a Service (RaaS), and ransomware professionals are maximizing attack revenue by selling stolen data, selling access, and practicing extortion for stolen confidential information. Encrypting the system is the last step in the RaaS revenue generation process. Ransomware professionals will try and return six to twelve months later to do it all again if security has not significantly improved.
Businesses need to enhance their security capabilities, not so much to keep attacks out, but to be able to detect, respond, and remediate intrusions before they become breaches. Enterprises need tools to identify atypical behavior and react to the situation quickly.
The Solution?
Using traditional approaches to security, will not address the increased risks. New security strategies are required to secure business processes and assets, regardless of where they are being used. Technology solutions have progressed to enhance security but also make it easier for staff to use with an enhanced experience.
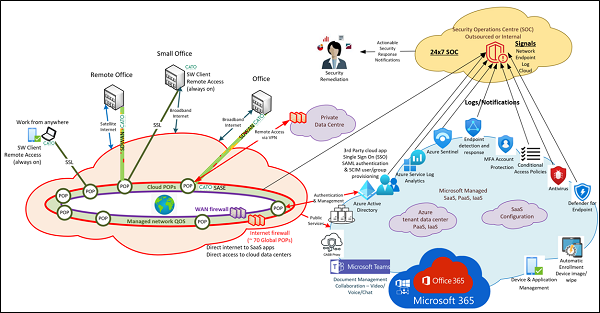
The key enhancements that have enhanced the security of remote and hybrid work (work from anywhere) have centered around two key cloud base security solutions: Zero Trust Platform as a Service (PaaS) and Secure Access Service Edge (SASE).
Both technologies can enable the business to empower remote and hybrid workers by providing a technology infrastructure that can provide a worker experience that is the same or similar when your staff are remote or in the office. The singular employee experience enhances security and the user experience.
Neither of these technology platforms are singular services but rather a collection of services that require a scale of infrastructure that would be historically unavailable to many businesses due to complexity and cost. Today, both technology platforms can be acquired as a service and managed by larger cloud service providers.
Zero Trust
Google, Amazon, Microsoft and others have adopted the concept of Zero Trust Security and turned them into a platform as a service solution . For Zero Trust to be effective, access to all resources must be evaluated, authorized and granted based on the integrated knowledge of the environment and the conditions under which access should be allowed. Zero Trust platforms enable and automate this using a framework that considers the identity, device, application, data, network, and infrastructure conditions to determine if access should be granted. A zero-trust service requires advanced artificial intelligence and machine learning.
SASE
Secure Access Service Edge (SASE) technologies combines networking and security functionality into a unified global cloud-based service offering. Many SASE solutions combine advanced cloud services for firewalls, remote access, application security, application priority and application performance
An effective SASE deployment is integrated with the Zero Trust authentication, is always on – in the office or remote, and is easy for staff to use. SASE ensures that application and data access is secure and consistent, regardless of the location, provided a reasonable Internet connection is available.
Integrated Security
SASE and Zero Trust technologies by themselves do not solve the problem. They are critical components of the solution. Using the full potential of these technologies can enable key functionality of an integrated security solution including:
- Centralized authentication with multi-factor authentication – to enhance and streamline application access
- Security management of identities, endpoints, cloud applications, on-premises applications, email, and documents – so that you know who is accessing what and when
- Deployment and management tools for all endpoints – to ensure that all devices can be rolled out according to security and user standards and can be recovered when it falls out of compliance
- Integrated logging and enable AI alerting – to provide an integrated view of what is happening in your environment
- Enable threat-hunting capabilities – to find intrusions before they become breaches
They provide many enhanced protection and detection capabilities but to be truly effective at enhancing security, they need to be integrated into a Security Operations Centre that can quickly respond to the signals of intrusion and remediate the situation before it becomes more serious and expensive.
Getting Started
Security does not start with technology. Improved security starts with good processes. Start with these steps and they will provide the basis for a successful Zero Trust and SASE deployment.
- Scope the challenge. Develop an asset register for the resources used by an organization to operate the business. These asset registers should log an organization's people, devices, software
- Evaluate the risks. Develop a risk register that considers confidentiality, integrity, availability, likelihood, and impact.
- Define your strategy for security by creating information security policies for managing information security activities.
- Use a trusted security framework (e.g., NIST-CSF, NIST-CMMC, ISO 27001) to guide your process and controls – creates a defendable checklist that is trusted by others in the industry.
- Leverage the big guys to use the zero trust and SASE security management tools on their platform as a service (PaaS).
Scott is writing on behalf of the SCTC, a premier professional organization for independent consultants. Our consultant members are leaders in the industry, able to provide best of breed professional services in a wide array of technologies. Every consultant member commits annually to a strict Code of Ethics, ensuring they work for the client benefit only and do not receive financial compensation from vendors and service providers.