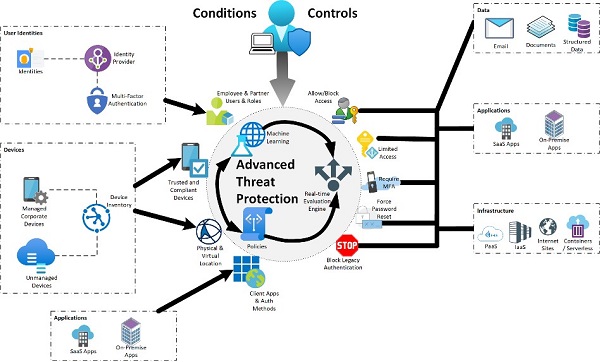
With the changing work-from-anywhere business and technology landscape, traditional techniques for protecting your systems and data are no longer enough. Ransomware as a service is a reality — and any business is at risk.
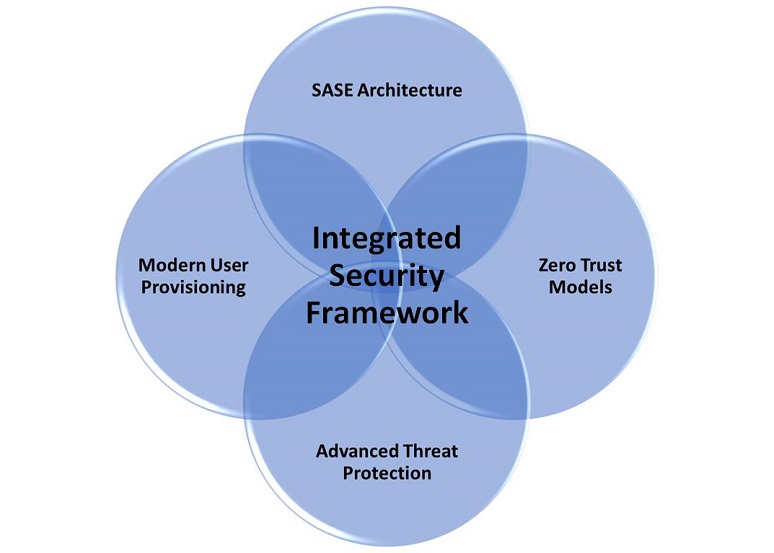
The good news is that we’ve seen significant cybersecurity advancements that, when combined into a next-gen integrated security framework, provide a strong foundation for success. They are:
- Modern user provisioning and authentication services
- Zero-trust model for all systems and services
- Secure access service edge (SASE) architecture
- Advanced threat protection (ATP) services
When integrated, as shown above, these services can provide a unified view of an enterprise’s security framework.
Modern User Provisioning and Authenication Services
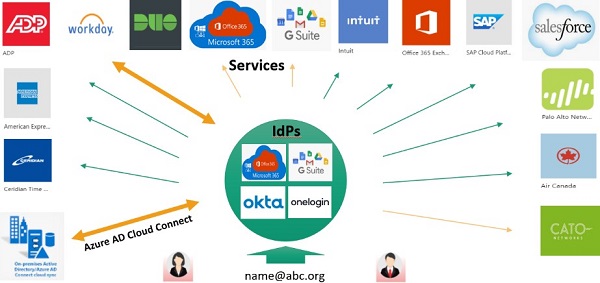
Modern user provisioning, single sign-on (SSO), or identity and access management (IAM) are different terms commonly used to describe a central source of authentication management and provisioning of access to application services, whether running on premises or in the cloud. IAM services provide the foundational platform for integration.
Modern user provisioning will simplify user registration and automate user provisioning, often via integration with the corporate HR information system or human capital management database, providing a single source of truth for your user community. Integration simplifies staff on-boarding and off-boarding processes, and reduces some security risks.
Allowing SSO access to staff, contractors, and partners will reduce the number of logins to remember and strengthen security. SSO will simplify the deployment and acceptance of multi-factor authentication (MFA), further enhancing authentication security and reducing risks.
Zero-Trust Model
A
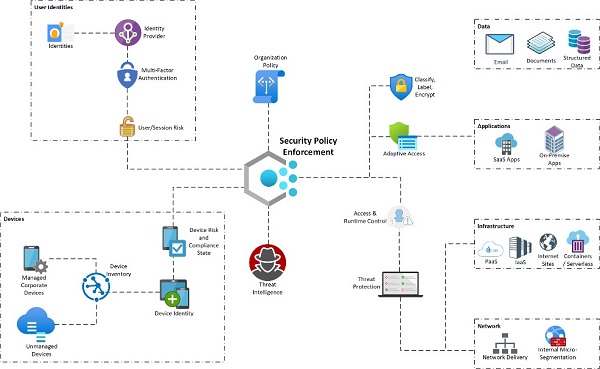
zero-trust model assumes breach and verifies each request as though it originates from an open network. Zero trust dispels the concept of trusted zones in a network.
Regardless of where the request originates, a zero-trust approach treats each application session as untrusted and requires authentication, authorization, and encryption before granting access. Zero trust, sometimes referred to as micro-segmentation, can help minimize lateral movement within an environment, making a cybercriminal's job much more difficult. A zero-trust model requires AI, analytics, and machine learning (ML) to detect and respond to threats in near-real-time.
Having a zero-trust model does not eliminate the need for an incident response plan. Rather, having the people, processes, and policy responses in place is even more important given that you’ll have significantly more insight into intrusions before they become breaches.
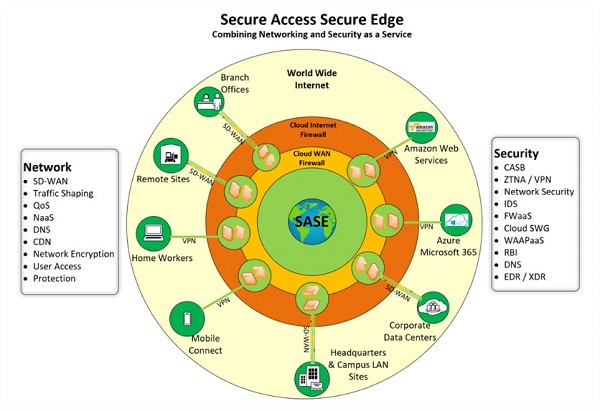
SASE Architecture
SASE combines networking and security functionality into a unified global cloud-based service that replaces remote VPN access and WANs. It’s most notable differentiator from traditional networking is that it is a cloud-native solution that is scalable, adaptable, provides global QoS, and is accessible from anywhere in the world. An essential security feature of SASE solutions is support for a zero-trust implementation model. SASE ensures that all sessions, no matter where they originate, are decrypted, inspected, and verified in real-time. SASE architecture improves the user application experience and reduces security risks — especially for cloud applications.
ATP
Modern provisioning, zero trust, and SASE provide a robust security foundation, but integration with advanced intelligence and analytics takes security to the next level. AI/ML-based tools enable threat hunting and alerting across user identities, endpoints (workstations, smartphones, servers, IoT devices, etc.), applications (both in the cloud and on premises), emails, and documents. These tools can look across activity logs to identify compromises and alert IT staff before a breach occurs. This proactive approach to security allows for faster response to incidents with fewer staff.
Integration
It should be emphasized that none of these modern cybersecurity tools should stand alone. Together they provide a framework to improve security operations. They require a shift in cybersecurity operations that focuses on rapid response and remediation of potential threats. People, processes, and next-gen technology can keep your business ahead of the cybercriminals and protect your business.
For more information from Data Perceptions on the integrated approach to security,
click here. And, for more information on
collaboration security, attend
Enterprise Connect 2021, taking place Sept. 27-29 in Orlando, Fla. As a No Jitter reader, you can save $200 off your registration using the promo code
NJAL200.
Scott is writing on the behalf of the SCTC, the premier professional organization for independent consultants. Our consultant members are leaders in the industry, able to provide best of breed professional services in a wide array of technologies. Every consultant member commits annually to a strict Code of Ethics, ensuring they work for the client benefit only and do not receive financial compensation from vendors and service providers.