UC interaction security has its own unique challenges, requirements, and solutions from standard Web and application transaction security, as I discussed earlier this year in a Enterprise Connect 2019
session and No Jitter
podcast. Here I’m going to dive into some advanced UC security functions and companies and products that are stepping up to help ensure these are available when and where required.
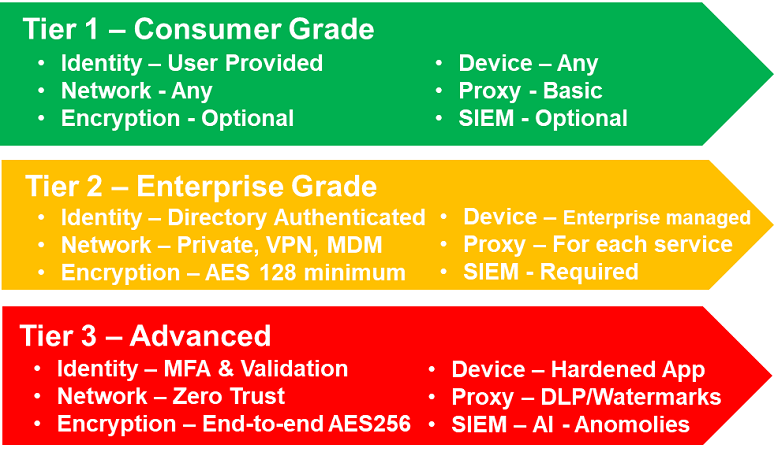
Figure 1, below, shows a three-tiered UC security model with consumer, enterprise, and advanced security grades. Based on discussions with 20 large enterprises, feedback shows that about 80% of enterprise UC interactions need consumer-grade security and 15% enterprise-grade, while 5% require advanced security. Advanced security is required for protecting intellectual property, for compliance requirements such as M&A deals, and to ensure privacy.
The first area of advancement is in a combination of identity management and ensuring multifactor authentication (MFA) along with validation and providing a hardened application to run on the end device. A couple of interesting companies to highlight are:
- Hotshot.mobi -- Its mission is to provide compliant messaging, collaboration, and identity management for business, built on a zero-trust foundation. Some of its unique features include the use of location and time as additional authentication factors. To receive a message, users must be at a geo-fenced location; optionally, the message can be set to expire after a period of time. One early use case is for deployment to a remediation team in need of a secure platform following an enterprise directory breach. Some incident response teams are proactively establishing secure off-band communications channels as part of their remediation and response plans by simply restricting all access to trusted members’ known locations.
- Journey.ai -- Remember Brett Shockley, onetime Avaya CTO, Cisco VP, and Spanlink CEO, and Michael Frendo, who had been EVP, Worldwide Engineering at Polycom? They and others have formed this company, which offers a zero-knowledge identity management network. One use case is for inbound and outbound calls between a bank and customer. The bank and the customer are able to validate one another biometrically, never having to exchange or store private information. The private data channel they establish has the added benefits of enabling zero-knowledge proofs of account and identity credentials, as well as eliminating the need for the customer to re-authenticate on agent transfer through an encrypted transfer of trust.
- Microsoft -- Microsoft, the market leader in enterprise identity management with its Active Directory platform, purchased LinkedIn for $26 billion in 2016. With all its work in the cloud, blockchain solutions, and LinkedIn data, it’s easy to see how Microsoft will be rolling out additional identity management services and incorporating them into its team collaboration application, Teams.
Stay tuned for more exciting products and services aimed at helping enterprises refine their digital relationship management strategies to ensure security, compliance, and privacy.
The second area is a combination of network encryption and anomaly detection. Last week at the Ribbon Perspective conference in Washington, D.C., Ribbon made a few announcements to help advance UC security. First, it is integrating its
SBC platform with 128 Technology to provide the underlying zero-trust networking and end-to-end FIPS 140-2 compliance. Second, it has launched the
Protect platform, which can take the logs from many different UC platforms, stitch them together, and use machine learning to ferret out suspicious activity such as toll fraud, robo-callers, registration attacks, and other suspicious activity.
A third area for advancement relates to data loss prevention and controlling and logging what information is going in and out of an organization. One way of doing this is using digital signatures. Zoom early this year
announced its support for audio signatures, which adds an ultrasonic watermark to audio streams so that UC admins have a way to identify the source of any leaked audio.
With the European Union’s General Data Protection Regulation, the California Consumer Privacy Act, and other regulations, along with regular breaches affecting businesses around the world, minimal compliance is no longer good enough. As a result, many enterprises are getting more proactive than ever regarding their security, privacy, and compliance strategies.