Securing today’s business environments is increasingly challenging. The threats are more widespread, and no business flies under malicious actors' radar. The technology landscape is more complex, thanks to a combination of hybrid workers, cloud applications, on-premises applications, privacy legislation, industry regulations, and integrated business processes spanning multiple business entities.
The enterprise needs to focus on the risks to operations. To address these risks, you need three primary classes of solutions.
- User/Application Access and Security
- User and Device Security
- Security Operations and Response
Your technology or operational processes need to integrate these three classes of solutions.
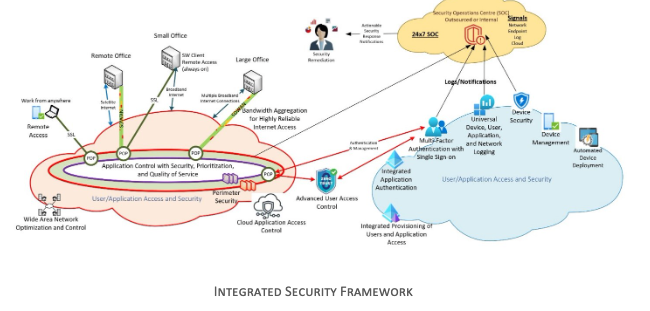
User/Application Access and Security
A business must establish secure connections between users, sites, data centers, cloud applications, on-premises systems, business partners, and trustworthy internet services. The big challenge today is that these users, sites, data centers, cloud applications, on-premises systems, business partners, and trustworthy internet services can be anywhere worldwide. These connections must be reliable and perform at the speed of business. Some typical security functions that are required, and why they are required, are:
- Wide Area Network Optimization and Control – connect your business assets and locations to each other.
- Bandwidth Aggregation for Highly Reliable Internet Access – increase connectivity reliability and capacity by bonding multiple connections, often referred to as SD-WAN.
- Application Control with Security, Prioritization, and Quality of Service – control what applications are used, where they are accessed, and the user experience of using the applications.
- Perimeter Security – manage secure application access control between users, business locations, and the Internet. In many cases, the network perimeter is no longer restricted to business locations and requires a solution that enables a universal experience, regardless of the user’s location.
- Remote Access – secure, always-on remote access that connects users to the perimeter security for wide area network and Internet access. Access should be user authenticated with single sign-on.
- Cloud Application Access Control – restrict what cloud applications are used by which staff and from which location.
- Advanced User Access Control – often referred to as Zero Trust, requires multiple levels of checks and conditions to be met when a user or system accesses applications and data. This will require integration into User and Device Security systems to be effective.
These solutions can be acquired as a cloud-based suite from vendors such as Cato Networks, Cisco, and Palo Alto and are typically marketed as Secure Access Service Edge (SASE).
User and Device Security
A business must control the security and user experience of all devices and systems with access to applications or data. Again, the big challenge is that these devices can be anywhere worldwide. Some typical functions that are required are:
- Automated Device Deployment – configure devices in an efficient and standardized manner with the applications required by the user.
- Device Management – manage, upgrade, and delete applications, data, and security settings on deployed devices.
- Device Security – centrally manage anti-virus, anti-malware, and firewall services. This function should be integrated with device management.
- Multi-Factor Authentication with Single Sign-on – control user authentication and access centrally and enforce multiple authentication factors.
- Integrated Application Authentication – enable applications to use centralized user identities (directory of users) for application-level authentication and permissions.
- Universal Device, User, Application, and Network Security Logging – centralize the collection and storage of security logs from devices, applications, and services to enable a complete view of security-related activities and potential threats.
- Integrated Provisioning of Users and Application Access – facilitate employee onboarding, change, and off-boarding to provide centralized data and application access and provisioning control. They are often accomplished by integrating human resources management and application authentication systems.
Vendors such as Microsoft, Google, Amazon, and Oracle often offer cloud-based suites that address all of the needs mentioned above.
Security Operations and Response
Prevention of security incidents is very important for an enterprise but the ability to detect and respond to a potential breach is even more important. The bad actors will penetrate your defenses, but early diagnosis and treatment of the infection can make all the difference. The critical functions needed to react to a compromise are:
- Security Awareness Training – training users (or human firewalls) in the organization to be aware of their security responsibilities and react when a compromise occurs. Training needs to be continuous and time effective for users.
- Security Log Analysis – machine learning, artificial intelligence, and human verification are used to analyze security logs for potential issues and threats.
- Centralized Actionable Security Notifications – the extension of the log analysis to create notifications of credible and actionable security remediation or response activities.
- Security Response Capabilities – the team or resources that respond to the notifications and remediate the risk promptly. Some remediation activities can be automated.
These solutions can be acquired from managed security and service providers (MSSP), managed detection and response (MDR) providers or outsourced security operation center (SOC) providers in
conjunction with internal staff. There are large and smaller providers depending on the location of the services required. Some international providers include eSentire, Artic Wolf, Palo Alto, and Alert Logic.
Getting Started …
IT security has become more challenging and complex. Organizations with smaller security operations teams must lean on larger security service providers to address the risks. Implementing an integrated set of cloud-based suites, that that span the functions discussed, will enable any enterprise to maintain strong IT security operations.
The business needs to start with the basics by understanding what they are trying to protect and the risks they are trying to prevent from happening.
- Scope the challenge. Develop an asset register for the resources used by an organization to operate the business. The asset register should log an organization's people, devices, data, and applications – and where these assets are kept and used: on-premises, cloud, data center, home office, partner site, etc.
- Evaluate the risks. Develop a risk register that considers confidentiality, integrity, availability, likelihood, and impact. This should also include other technology dependencies.
By using the asset register and understanding the risks the business wants to prevent, detect, and recover, business leaders can start understanding what needs to be done. This understanding provides the basis for a technology security strategy from a business perspective. Business policies can be written to define your strategy for security and managing information security activities. A trusted security framework like NIST-CSF, NIST-CMMC, or ISO 27001 can guide these policies.
These policies will drive the conditions for user/application access and security, user and device security, and security operations and response.
Scott is writing on behalf of the SCTC, a premier professional organization for independent consultants. Our consultant members are leaders in the industry, able to provide best of breed professional services in a wide array of technologies. Every consultant member commits annually to a strict Code of Ethics, ensuring they work for the client benefit only and do not receive financial compensation from vendors and service providers.