Becoming a hyper-connected enterprise is one of the foundational components of digital transformation (DX). I’ve written a number of reports and posts on DX and one of the recommendations I always make is “connect everything,” as it’s this sort of hyper-connectivity that enables businesses to create new processes, change the way people work, and compete better with its peers.
However, as is the case with most things in life, for every yin there’s a yang, and in the case of hyper-connectivity, the downside is increased complexity for the IT and security teams to manage.
Despite efforts to try and get a handle on all of the new consumer, Internet of Things (IoT), and business-critical devices being connected to the network, operations teams are actually falling behind. It’s important to understand the magnitude of the tasks facing IT teams. With the rise of BYOD, businesses went from having just over one device per person, to at least three or four. And now with IoT, physical security, line-of-business systems, and other non-IT devices, this number jumps orders of magnitude. The number of devices is now so high that trying to count devices per user is meaningless.
In something like a hospital setting, it’s possible to have only a few thousand users but over a hundred thousand devices. One data point that highlights the struggles for IT comes from a recent ZK Research survey, which found that 61% of respondents had no or low confidence that they knew all the devices connected to the network; this is up sharply from 51% five years ago. This indicates that IT, security, and operations simply can’t match the scale of the problem.
Calling for Order
This week, a new venture-backed company, called Ordr, launched, with promises to help IT, security, and operations teams get a handle on managing and securing all of these devices with an artificial intelligence (AI)-based, closed-loop management platform. The leadership team has a tremendous amount of experience in managing densely connected environments, as most of them came from Aruba Networks. Key members of the leadership team include:
- CEO Greg Murphy, former Senior VP of business operations and strategy at Aruba
- Co-founder Pandian Gnanaprakasam, former chief development officer at Aruba
- Co-founder Sheausong Yang, former VP of technology at Aruba
- Chairman of the Board Dominic Orr, former CEO of Aruba (pre HPE acquisition)
Having Orr as chairman will be a real boon to Ordr. I’ve known Orr for years and watched him take Aruba from a small, niche Wi-Fi company through its IPO, culminating with the sale of Aruba to HPE for $3 billion. Despite constant rumors that Cisco would run it over, under Orr’s leadership Aruba not only survived, but thrived.
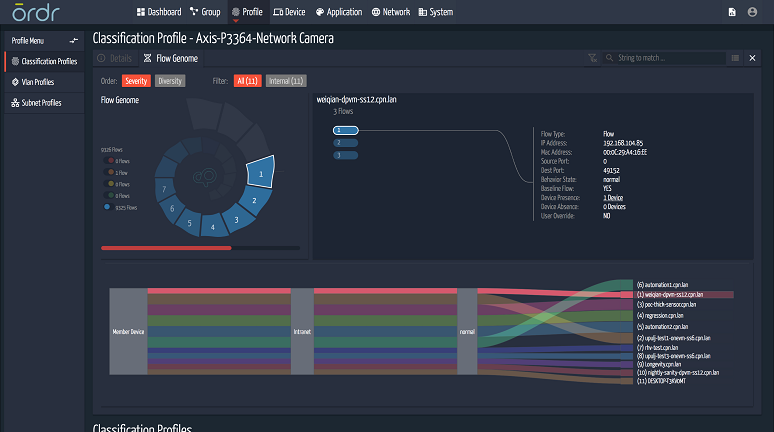
Ordr’s product, Systems Control Engine (SCE) is a purpose-built management tool that fully maps what it calls the “device flow genome” at massive scale. In layman’s terms, this means it understands the flow of data, at a granular level, for every device connected to the company network.
SCE uses AI to analyze the data to dynamically create policies for each class of device -- policies that are constantly being validated and enforced. Ordr has built a massive and growing database of connected devices, including medical equipment, HVAC systems, IP cameras, engineering systems, and a lot more. Because it understands the baseline flow genome, SCE is able to pick up even the most miniscule behavioral change that could indicate a breach. For example, a business may have deployed a cloud-managed IP video endpoint that sends updates to the cloud provider daily. If the Ordr SCE sees it attempting to access another company resource, like an accounting server, it can automatically quarantine it.
The closed-loop model enables it to regulate and secure all connected devices and then enforce the AI-generated micro-segmentation polices. This is critical in minimizing the “blast radius” of a breach. In the above example, the SCE may have auto-generated a policy stating that all conference equipment is to be placed in a secure segment. That way, when a device is breached, it has no access to other critical resources, minimizing damage.
It’s important to note that Ordr operates as an overlay to the existing network and security infrastructure, and integrates with all the big-name vendors such as Cisco, HPE, Palo Alto Networks, and Fortinet. No forklift upgrades or agents are required.
The use of AI is key to Ordr’s ability to analyze the data and connect the dots between them. It’s long been my opinion that a hyper-connected organization can’t be secured or managed without AI. Ordr’s AI-based management platform can answer many key questions that people can’t using manual methods, including the following:
- What is connected? AI can automate the identification, classification, and location of all network-connected devices and systems, eliminating blinds spots.
- What, exactly, are the devices doing? AI can fully map all connected device communications flow detail to quickly spot anomalous behavior.
- Which systems are vulnerable? AI assesses exposed weaknesses in real-time and at scale to determine potential risk.
- How can the critical devices and systems be regulated and protected? AI automates the generation, implementation, and enforcement of security policies; the closed-loop model ensures policies follow devices without manual reconfiguration.
- Are the systems being used efficiently? AI can provide accurate usage and utilization information.
The last bullet is important, as Ordr didn’t build SCE just for security teams, although given the focus of cybersecurity today, one could argue that’s the low-hanging fruit. IT operations and lines of business can use the analytics to ensure devices are being used efficiently and redeploy if necessary.
For example, a hospital may see that infusion pumps on one floor are over 90% utilization while on another utilization is under 20%. The decision could be made then to move some of the assets to maximize utilization. In a carpeted office, conference room equipment usage can be measured and then the configurations of the rooms can be optimized to better meet demand.
It will be interesting to see if Ordr can have success as a multi-dimensional tool. Many vendors have tried in the past to appeal to IT and security operations, but most have failed. Not because the product didn’t work, but more because of silos within the technology groups. However, the timing may be right for Ordr as many leading CIOs and CISOs I’ve interviewed recently have talked about the importance of breaking down the historical walls that separate groups like network and security operations. Five years ago, the approach Ordr is taking may not have worked, but IT and security teams are feeling the weight of IoT and hyper-connectedness and well-run companies have brought the groups together.
The number of connected devices continues to grow exponentially, creating a serious problem for businesses. Rapid expansion without the right tools in place will lead to chaos and breaches, like Target experienced a few years ago. An AI-based management tool needs to be in place so IT and security teams can see, secure, and manage what they need to.